Android Deobfuscate Stack Trace Which is Very Interesting
One of the problems of Android application support is to deofuscate or retrace stack traces obtained from an obfuscated release build. Upload the ProGuard mapping file for the version of your app.

How To Deobfuscate An Android Stacktrace Using Mapping File
The Google Play Console reports native crashes under Android vitals.

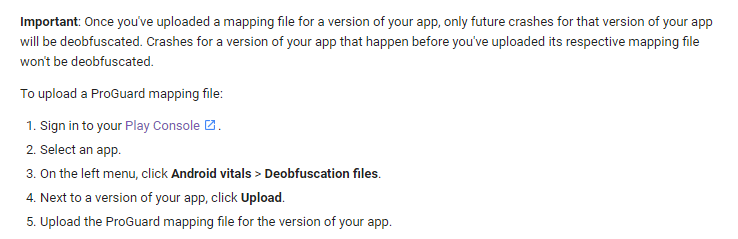
Android deobfuscate stack trace. Step 02 – Read the mapping file. Next to a version of your app click Upload. Add your mapping file and obfuscated stack trace.
Deobfuscate or symbolicate crash stack traces Step 1. Locate the the retrace tool in the Android SDK directory it will be in toolsproguardbinretracesh or in Windows it will be toolsproguardbinretracebat. The standard way of obfuscation in Android development is done using tools such as the ProGuard.
In the Android Studio menu bar navigate to Analyze Analyze Stack Trace or Thread Dump Paste the stack trace in the window Click Normalize to format the stack trace -. You need to deobfuscate your stack trace. The Android Developer docs page pretty much explains how to use this tool but Ill summarize the steps here.
How to deobfuscate crashes In order to deobfuscate your crashes you need to upload a reference for the debug symbols that got stripped. Instead I see the original stack trace. On the left menu click Android vitals Deobfuscation files.
You can also decode by hand using the contents of. Tingnan ang mga na-deobfuscate na stack trace ng pag-crash. Run the proguardgui tool to retrace it.
To do that you can do the following steps. Sign in to your Play Console. As part of Appdomes protection for applications Appdome offers Control-Flow Relocation to any iOS mobile app.
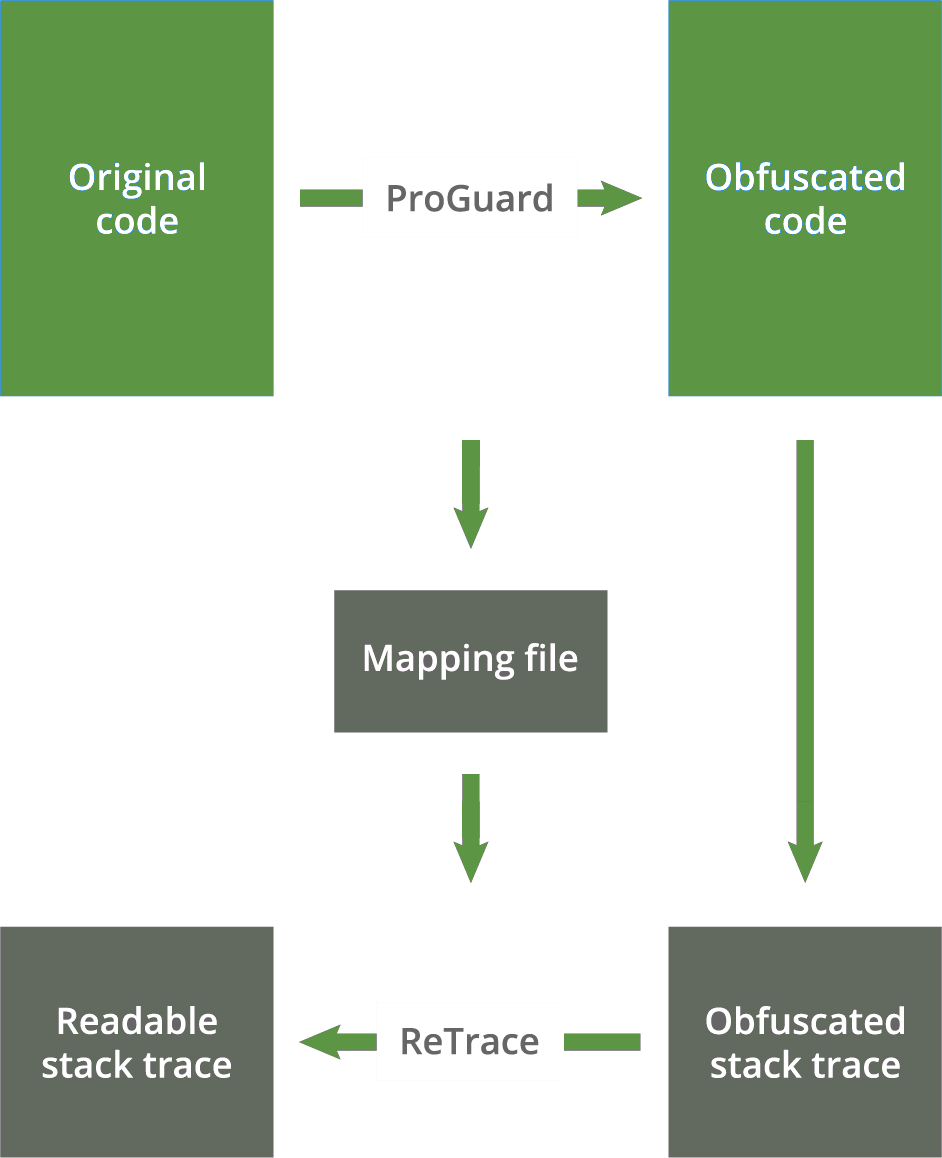
I expect to see the stack trace deobfuscated but I dont. To figure out how to deobfuscate a stack trace you need to understand how the obfuscation actually works. This reference is called a mapping file.
LibraryAndroidsdktoolsproguardbinretracesh -verbose buildappoutputsmappingreleasemappingtxt Desktopobfuscated_tracetxt. – Read the below stack error report. Deobfuscation is the process of transforming these stack traces active memory addresses into something human-readable in terms of methods and functions.
Use generated mappingtxt to deobfuscate code. If you enjoyed this article please dont forget to Clap. Make sure the source code youre viewing is from the exact same version of.
Understand the stack trace error report. To get the same highlighted and clickable view of an external stack trace from a bug report follow these steps. When you read these logs it becomes difficult to understand and to locate the exact error.
This file enables symbolicated native crash stack traces that include class and function names in. Read the mapping file. From the left menu click Android vitals Deobfuscation files.
To make use of any stack traces from your Android Market account you can use your map file produced with the-printmapping option in the ProGuard config with ReTrace ProGuard companion tool to decode the stack trace. Upload a deobfuscation or symbolication file To deobfuscate or symbolicate your apps crashes and ANRs for a. After doing so to view your deobfuscated crash stack traces.
Kung gumagamit ka ng Android App Bundle at bersyon ng plugin ng Android Gradle na 41 o mas bago wala ka nang gagawin. With a few steps you can generate and upload a native debug symbols file for your app. Awtomatiko naming kukunin ang file ng deobfuscation mula sa bundle at makakalaktaw ka sa Hakbang 3.
Appdomes deobfuscation tool allows the application owner to recover the correct stack trace from the crash report. From the Analyze menu click Analyze Stack Trace. Copy paste your obfuscated stack trace from Bugfender to a text file ex.
Sign in to your Play Console. You can invoke it from the Analyze menu or with the usual Find action dialog seriously you should use that like all the time. Select ReTrace in the left column.
Let me know your way to de-obfuscate the stack trace. Analyze Stack Traces in Android Studio Using the Anaylze Stack Trace tool In the Android Studio menu bar navigate to Analyze Analyze Stack Trace or Thread Dump Paste the It creates a fully clickable stack trace as if it were originating in the logcat panel. This Knowledge Base article provides step-by-step instructions for getting and using Appdomes deobfuscation tool.
Generate a deobfuscation or symbolication file To deobfuscate or symbolicate your apps crashes and ANRs for a. Open your project in Android Studio. To deobsfucate a stack trace load the corresponding mapping file copy and paste the obsfucated stack trace and click Deobfuscate.

Android What Is Proguard And Proguard Mapping Stack Overflow
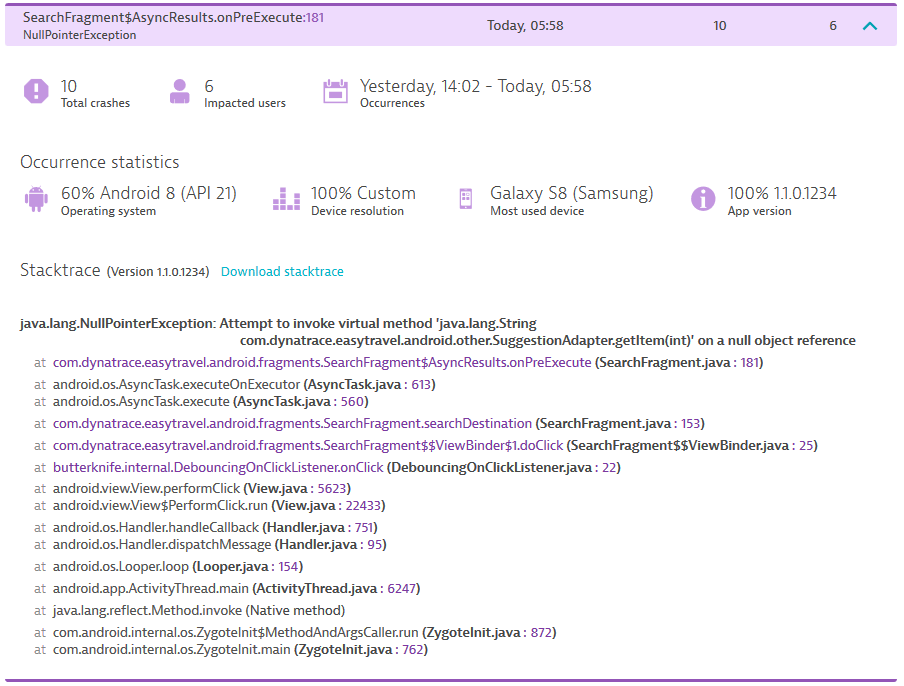
Understand Mobile App Crashes Effectively With Our Mobile Symbol Service And Ios Symbolication Preview Dynatrace News

How To Use Retrace Bat In Android Stack Overflow

Appcenter Cannot Deobfuscate Android R8 Code Issue 458 Microsoft Appcenter Github

Where Does Android Studio Save The Proguard Mapping File Stack Overflow

How To Deobfuscate An Android Stacktrace Using Mapping File

How To Get Crashlytics Stacktraces Deobfuscated Issue 897 Firebase Quickstart Android Github

Unable To Deobfuscate Stack Trace Even When Mappings Txt Is Uploaded Issue 631 Getsentry Sentry Java Github

How To Deobfuscate An Android Stacktrace Using Mapping File

Stack Trace Isn T Being De Obfuscated For Andorid R8 Code Shrinker Issue 6 Getsentry Rust Proguard Github

Stack Trace Isn T Being De Obfuscated For Andorid R8 Code Shrinker Issue 6 Getsentry Rust Proguard Github
Deobfuscation With Proguard S Mapping Xml By Tejshree Yeole Medium

Easy Mode For Using Proguard In Android Stack Overflow

How To Deobfuscate An Android Stacktrace Using Mapping File

How To Deobfuscate An Android Stacktrace Using Mapping File

Seamlessly Integrate Dynatrace Mobile Crash Reporting Into Your Build Environments M Square

How To Deobfuscate An Android Stacktrace Using Mapping File
Deobfuscation With Proguard S Mapping Xml By Tejshree Yeole Medium
De Obfuscate Stack Traces For More Stories By Maheshwar Ligade Techwasti Medium

Post a Comment for "Android Deobfuscate Stack Trace Which is Very Interesting"